Security module: Difference between revisions
(Added Trends in PUF) |
|||
| (14 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
==Security Module and Hardware Key Generation== | ==Security Module and Hardware Key Generation== | ||
The pervasiveness and vast number of deployed nodes monitoring the environment makes security a fundamental challenge, especially in IoT applications. Security issues are expected to arise in terms of data authenticity, integrity, and confidentiality. Data as well as the sender of this data need to be verified and security must be assured down to the hardware level (i.e., each node needs to be confirmed to be). Security can be inserted in several levels. Chip authentication is necessary when nodes are added onto the network. Data sent between the nodes can also be secured via lightweight encryption. Finally commands for actuation need to be authenticated and verified. All these can be enhanced through machine learning. | The pervasiveness and vast number of deployed nodes monitoring the environment makes security a fundamental challenge, especially in IoT applications. Security issues are expected to arise in terms of data authenticity, availability, integrity, and confidentiality<ref>T. Zia and A. Zomaya, "Security Issues in Wireless Sensor Networks," 2006 International Conference on Systems and Networks Communications (ICSNC'06), 2006, pp. 40-40, doi: 10.1109/ICSNC.2006.66.</ref>. Data as well as the sender of this data need to be verified and security must be assured down to the hardware level (i.e., each node needs to be confirmed to be). Security can be inserted in several levels. Chip authentication is necessary when nodes are added onto the network. Data sent between the nodes can also be secured via lightweight encryption. Finally commands for actuation need to be authenticated and verified. All these can be enhanced through machine learning. | ||
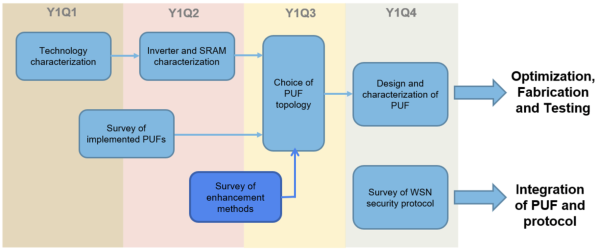
Year 1 of this project focuses on the use of physically unclonable functions (PUFs) as unconditionally secure hardware key | Year 1 of this project focuses on the use of physically unclonable functions (PUFs) as unconditionally secure hardware key. The activities for this year are shown in the figure below. | ||
[[File:Sec-year1 activities.png|center|thumb|600x600px|Figure 1. Year 1 Activities for the Security Module.]] | |||
[[File: | |||
==Physically Unclonable Functions== | ==Physically Unclonable Functions== | ||
In the recent past, Physically Unclonable Functions (PUFs) have emerged as potentially highly secure and lightweight solution to ensure data and hardware security, assuring trustworthiness down to the chip level<ref>R. Maes, V. Rozic, I. Verbauwhede, P. Koeberl, E. van der Sluis, V. can der Leest, "Experimental Evaluation of Physically Unclonable Functions in 65 nm CMOS", in European Solid State Circuit Conference (ESSCIRC), 2012, pp. 486489.</ref>. A PUF is a function that maps an input (digital) challenge to an output (digital) response in a repeatable but unpredictable manner, leveraging on chip-specific random process variations. Machine learning was also proposed to improve authentication with PUF<ref>B. Chatterjee, D. Das, S. Sen, "RF-PUF: IoT Security Enhancement through Authentication of Wireless Nodes using In-situ Machine Learning", IEEE International Symposium on Hardware Oriented Security and Trust (HOST), 2018, pp. 205-208. </ref>. | In the recent past, Physically Unclonable Functions (PUFs) have emerged as potentially highly secure and lightweight solution to ensure data and hardware security, assuring trustworthiness down to the chip level<ref>R. Maes, V. Rozic, I. Verbauwhede, P. Koeberl, E. van der Sluis, V. can der Leest, "Experimental Evaluation of Physically Unclonable Functions in 65 nm CMOS", in European Solid State Circuit Conference (ESSCIRC), 2012, pp. 486489.</ref>. A PUF is a function that maps an input (digital) challenge to an output (digital) response in a repeatable but unpredictable manner, leveraging on chip-specific random process variations. Machine learning was also proposed to improve authentication with PUF<ref>B. Chatterjee, D. Das, S. Sen, "RF-PUF: IoT Security Enhancement through Authentication of Wireless Nodes using In-situ Machine Learning", IEEE International Symposium on Hardware Oriented Security and Trust (HOST), 2018, pp. 205-208. </ref>. | ||
PUFs have 3 main properties: randomness, uniqueness and reliability<ref>A. Alvarez and M. Alioto, “Security down to the Hardware Level,” in Enabling the Internet of Things - from Circuits to Networks, Springer, 2017.</ref>. Randomness refers to the bias of the generated key, or the ratio between logic 1 and logic 0 bits in the key (ideally, the bias would be 50%). Uniqueness is measured through the inter-PUF hamming distance fraction, or the percentage of PUF bits that are different between keys. Ideally, we would want a hamming distance fraction of 50%. Reliability, on the other hand measures the intra-PUF hamming distance or the bit error rate (BER) over several trials and under process, voltage and temperature (PVT) variations. Ideally, the BER should be 0, signifying no change in bits in the | |||
PUFs have 3 main properties: randomness, uniqueness and reliability<ref>A. Alvarez and M. Alioto, “Security down to the Hardware Level,” in Enabling the Internet of Things - from Circuits to Networks, Springer, 2017.</ref>. Randomness refers to the bias of the generated key, or the ratio between logic 1 and logic 0 bits in the key (ideally, the bias would be 50%). Uniqueness is measured through the inter-PUF hamming distance fraction, or the percentage of PUF bits that are different between keys. Ideally, we would want a hamming distance fraction of 50%. Reliability, on the other hand measures the intra-PUF hamming distance or the bit error rate (BER) over several trials and under process, voltage and temperature (PVT) variations. Ideally, the BER should be 0, signifying no change in bit values despite PVT variations. | |||
The concept of using device mismatches for started in the year 2000 with the IC identification (ICID) <ref>K. Lofstrom, W. R. Daasch, and D. Taylor, “IC Identification Circuit using Device Mismatch,” ISSCC Dig. Tech. Papers, 2000, pp. 372–373.</ref>. Using delay differences due to random mismatch was shown to also give the same function with the arbiter PUF <ref>J. W. Lee, B. Gassend, G. E. Suh, M. van Dijk, and S. Devadas, “A Technique to Build a Secret Key in Integrated Circuits for Identification and Authentication Applications,” IEEE Symp. VLSI Circuits, 2004, pp. 176–179.</ref><ref>D. Lim, J. W. Lee, B. Gassend, G. E. Suh, M. Van Dijk, and S. Devadas, “Extracting Secret Keys from Integrated Circuits,” IEEE Trans. Very Large Scale Integr. Syst., vol. 13, no. 10, pp. 1200–1205, 2005.</ref>. One of the most common delay-based PUFs is the ring oscillator (RO) PUF,<ref>R. Maes, V. Rozic, I. Verbauwhede, P. Koeberl, E. van der Sluis, and V. can der Leest, “Experimental Evaluation of Physically Unclonable Functions in 65 nm CMOS,” in European Solid State Circuit Conference (ESSCIRC), 2012, pp. 486–489.</ref> where the frequencies of a pair of ring oscillators are compared and decide the bit value (e.g. 1 if fB > fA). The power-on sate of memory elements can also be used to generate the hardware key, as demonstrated with the latch PUF<ref>Y. Su, J. Holleman, and B. Otis, “A 1.6pJ/bit 96% Stable Chip-ID Generating Circuit using Process Variations,” ISSCC Dig. Tech. Papers, 2007, pp. 406–408.</ref>, and more recently even for the RRAM crossbar<ref>Y. Pang, B. Gao, D. Wu, S. Yi, Q. Liu, W.-H. Chen, T.-W. Chang, W.-E. Lin, X. Sun, S. Yu, H. Qian, M. F. Chang, H. Wu, "A Reconfigurable RRAM PUF Utilizing Post-Process Randomness Source with <6×10-6 N-BER," 2019 IEEE International Solid- | |||
State Circuits Conference - (ISSCC), San Francisco, CA, USA, 2019, pp. 402-403.</ref>. Leveraging on the memory cell's metastability <ref>S. K. Mathew, S. K. Satpathy, M. A. Anders, H. Kaul, S. K. Hsu, A. Agarwal, G. K. Chen, R. J. Parker, R. K. Krishnamurthy, and V. De, “A 0.19pJ/b PVT-Variation-Tolerant Hybrid Physically Unclonable Function Circuit for 100% Stable Secure Key Generation in 22nm CMOS,” ISSCC Dig. Tech. Papers, pp. 278–280.</ref>. Other types of PUFs have also been explored, such as the VIA PUF<ref>B. D. Choi, T. W. Kim, and D. K. Kim, “Zero bit error rate ID generation circuit using via formation probability in 0.18 µm CMOS process,” IET Journals Mag., vol. 50, no. 12, pp. 876–877, 2014.</ref> and oxide rupture PUF<ref>M.-Y. Wu, T.-H. Yang, L.-C. Chen, C.-C. Lin, H.-C. Hu, F.-Y. Su, C.-M. Wang, J. P.-H. Huang, H.-M. Chen, C. C.-H. Lu, E. C.-S. Yang, R. S.-J. Shen, “A PUF Scheme Using Competing Oxide Rupture with Bit Error RateApproaching Zero,” in IEEE International Solid State Circuits Conference (ISSCC), 2018, pp. 130–132.</ref>, to name a few. | |||
{| class="wikitable" style="width: 70%;" | |||
|- | |||
! PUF Name !! ICID !! Arbiter !! Latch !! RO !! INV_PUF !! VIA !! Oxide !! RRAM | |||
|- | |||
| Type | |||
|| Analog | |||
|| Delay | |||
|| Memory | |||
|| Delay | |||
|| Monostable | |||
|| others | |||
|| others | |||
|| NVM | |||
|- | |||
| Technology (nm) | |||
|| 350 | |||
|| 180 | |||
|| 130 | |||
|| 65 | |||
|| 65 | |||
|| 180 | |||
|| 55 | |||
|| 130 | |||
|- | |||
| Worst Native Instability at Nominal Condition (%) | |||
|| 1.3 | |||
|| 4.82 | |||
|| 3.04 | |||
|| 2.8 | |||
|| 2.34 | |||
|| N/A | |||
|| N/A | |||
|| 0.0006 | |||
|- | |||
| Nominal Voltage | |||
|| 2.5 | |||
|| 1.8 | |||
|| 1 | |||
|| 1.2 | |||
|| 1 | |||
|| 1.8 | |||
|| 1 | |||
|| 5.5 | |||
|- | |||
|Maximum Instability under PVT Variation (%) | |||
|5 | |||
|4.82 | |||
|5.46875 | |||
|3.9 | |||
|5.72 | |||
|<nowiki>--</nowiki> | |||
|<nowiki>--</nowiki> | |||
|0.0006 | |||
|- | |||
|Voltage Range (V) | |||
|1.1-5 | |||
|1.8+/-2% | |||
|0.9-1.2 | |||
|1.2 | |||
|0.6-1 | |||
|0.01904 | |||
|0.0000238 | |||
|0.0006 | |||
|- | |||
|Temperature Range (C) | |||
|<nowiki>-25-125</nowiki> | |||
|27-70 | |||
|N/A | |||
|<nowiki>-40,25,90</nowiki> | |||
|25-85 | |||
|1.6-2 | |||
|0.8-1.4 | |||
|2.5-5.5 | |||
|- | |||
|Bit Error Rate (%) | |||
|N/A | |||
|4.82 | |||
|5.46875 | |||
|N/A | |||
|N/A | |||
|6 | |||
| | |||
| | |||
|- | |||
|BER after stability enhancement | |||
|N/A | |||
|N/A | |||
|N/A | |||
|N/A | |||
|N/A | |||
|0.01904 | |||
|0.0000238 | |||
|0.0006 | |||
|- | |||
|Energy per bit (pJ/bit) | |||
|8333.333333 | |||
|0.17125 | |||
|0.93 | |||
|N/A | |||
|0.015 | |||
|N/A | |||
|5.2 | |||
|3.028 | |||
|- | |||
|Area (sq.um) | |||
|23436 | |||
|1468944 | |||
|9450 | |||
|241000 | |||
|6000 | |||
|1.06E+05 | |||
| | |||
|2.86 | |||
|- | |||
|Bits | |||
|112 | |||
|64 | |||
|180 | |||
|3840 | |||
|3040 | |||
|128 | |||
| | |||
|8.19E+03 | |||
|- | |||
|Area per bit (F<sup>2</sup> / bit) | |||
|1708.163265 | |||
|708402.7778 | |||
|3106.508876 | |||
|14854.53649 | |||
|6000 | |||
|1.05E+06 | |||
|218.2 | |||
|169.2 | |||
|- | |||
|Bias | |||
|N/A | |||
|N/A | |||
|N/A | |||
|N/A | |||
|0.5015625 | |||
|N/A | |||
| | |||
|0.5 | |||
|- | |||
|Inter-PUF FHD | |||
|0.4910714286 | |||
|0.38 | |||
|0.50546875 | |||
|0.495 | |||
|0.5013671875 | |||
|N/A | |||
| | |||
|1 | |||
|- | |||
|Intra-PUF FHD | |||
|0.013392857 | |||
|0.02 | |||
|3.04 | |||
|0.028 | |||
|0.0033636719 | |||
|N/A | |||
|0.031 | |||
|0.044 | |||
|- | |||
|# of possible CRPs | |||
|132 | |||
|4.5036E+15 | |||
|1 | |||
|256 | |||
|11 | |||
|1 | |||
| | |||
|64 | |||
|} | |||
== Trends in PUF == | |||
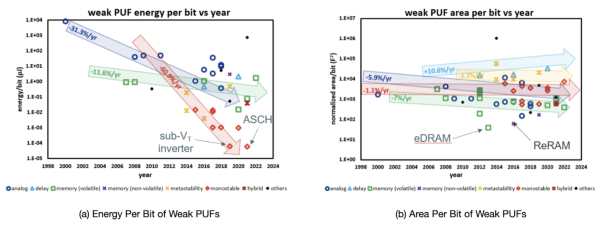
[[File:Energy and Area PUF Trend.png|thumb|600x600px|Figure 2. Energy and Area Per Bit of Weak PUFs.]] | |||
Looking at PUFs implemented on ASIC, we can see that the majority of the PUFs are still weak PUFs, that is, they have limited challenge-response pairs (CRPs), as opposed to strong PUFs. Some of the trends in terms of area, stability and energy are shown in the figures on the right, and can be found in the PUFdb<ref>M. Alioto, A. Alvarez, "Green IC Physically Unclonable Function database," [Online]. Available: http://www.green-ic.org/pufdb.</ref> and HWsecdb<ref>M. Alioto, “HW security primitives database," [Online]. Available: http://www.green-ic.org/hwsecdb</ref>, which are public databases of PUFs, TRNGs and other hardware security implementations in ASIC. | |||
Figure 2 shows the energy per bit and area per bit of existing implemented PUFs. These two metrics are important for resource-limited systems like WSN. It can be seen in Figure 3a that those with lowest energy to date are monostable PUFs, specifically the Automatic Self Checking and Healing (ASCH)<ref>Yan He et al. “An Automatic Self-Checking and Healing Physically Unclonable Function (PUF) with < 3x10−8 Bit Error Rate”. In: IEEE International Solid-State Circuits Conference. Vol. 64. February. 2021, pp. 506–508. </ref> PUF and sub-threshold inverter<ref>Dai Li and Kaiyuan Yang. “25.1 A 562F2 Physically Unclonable Function with a Zero-Overhead Stabilization Scheme”. In: 2019 IEEE International Solid- State Circuits Conference - (ISSCC). 2019, pp. 400–402.</ref>. In terms of area, the smallest are the memory bitcells, specifically the eDRAM PUF<ref>Sami Rosenblatt et al. “Field Tolerant Dynamic Intrinsic Chip ID Using 32 nm High-K/Metal Gate SOI Embedded DRAM”. In: IEEE Journal of Solid State Circuits (JSSC) 48.4 (2013), pp. 940–947.</ref> and the ReRAM PUF<ref>Y Yoshimoto et al. “A ReRAM-based Physically Unclonable Function with Bit Error Rate ¡ 0.5% after 10 years at 125◦C for 40nm Embedded Application”. In: Symposium on VLSI Technology. 2016, pp. 256–257.</ref>. | |||
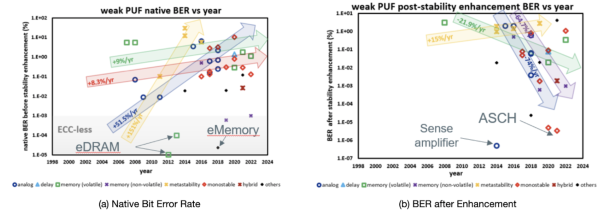
[[File:BER Trend in PUF.png|thumb|600x600px|Figure 3. Bit Error Rate of Weak PUFs.]] | |||
One important property of PUFs is the bit error rate (BER), which specifies the percentage of bits that flip after several readings. Figure 3a shows the BER of weak PUFs implemented to date. The PUFs with low native BER are the memory PUFs, specifically the eDRAM PUF<ref>Sami Rosenblatt et al. “Field Tolerant Dynamic Intrinsic Chip ID Using 32 nm High-K/Metal Gate SOI Embedded DRAM”. In: IEEE Journal of Solid State Circuits (JSSC) 48.4 (2013), pp. 940–947.</ref>, with BER in the order of 10<sup>−5</sup> and the eMemory<ref>Meng-Yi Wu et al. “A PUF Scheme Using Competing Oxide Rupture with Bit Error Rate Approaching Zero”. In: IEEE International Solid State Circuits Conference (ISSCC). 2018, pp. 130–132.</ref>. These, however, are greatly reduced after applying enhancement techniques such as masking, ECC and majority voting. After stability enhancement, the BER can go an order lower, and the PUF with lowest BER after enhancement is the sense amplifier based PUF<ref>Mudit Bhargava and Ken Mai. “An efficient reliable PUF-based cryptographic key generator in 65nm CMOS”. In: Design, Automation & Test in Europe Conference & Exhibition (DATE). Vol. 1. IEEE Conference Publications, 2014, pp. 1–6.</ref>. | |||
==Curriculum and Manpower Development== | ==Curriculum and Manpower Development== | ||
As part of the objective of the CIDR program to continuously improve the curriculum and manpower, the topic on physically unclonable functions was incorporated in the EE 226 (Digital Integrated Circuits) as a possible area of research. The introduction lecture can now be found in youtube<ref>https://youtu.be/JfNnSYuIOkc</ref>. | As part of the objective of the CIDR program to continuously improve the curriculum and manpower, the topic on physically unclonable functions was incorporated in the EE 226 (Digital Integrated Circuits) as a possible area of research. The introduction lecture can now be found in youtube<ref>https://youtu.be/JfNnSYuIOkc</ref>. | ||
==References== | ==References== | ||
Latest revision as of 18:35, 28 June 2023
Security Module and Hardware Key Generation
The pervasiveness and vast number of deployed nodes monitoring the environment makes security a fundamental challenge, especially in IoT applications. Security issues are expected to arise in terms of data authenticity, availability, integrity, and confidentiality[1]. Data as well as the sender of this data need to be verified and security must be assured down to the hardware level (i.e., each node needs to be confirmed to be). Security can be inserted in several levels. Chip authentication is necessary when nodes are added onto the network. Data sent between the nodes can also be secured via lightweight encryption. Finally commands for actuation need to be authenticated and verified. All these can be enhanced through machine learning.
Year 1 of this project focuses on the use of physically unclonable functions (PUFs) as unconditionally secure hardware key. The activities for this year are shown in the figure below.
Physically Unclonable Functions
In the recent past, Physically Unclonable Functions (PUFs) have emerged as potentially highly secure and lightweight solution to ensure data and hardware security, assuring trustworthiness down to the chip level[2]. A PUF is a function that maps an input (digital) challenge to an output (digital) response in a repeatable but unpredictable manner, leveraging on chip-specific random process variations. Machine learning was also proposed to improve authentication with PUF[3].
PUFs have 3 main properties: randomness, uniqueness and reliability[4]. Randomness refers to the bias of the generated key, or the ratio between logic 1 and logic 0 bits in the key (ideally, the bias would be 50%). Uniqueness is measured through the inter-PUF hamming distance fraction, or the percentage of PUF bits that are different between keys. Ideally, we would want a hamming distance fraction of 50%. Reliability, on the other hand measures the intra-PUF hamming distance or the bit error rate (BER) over several trials and under process, voltage and temperature (PVT) variations. Ideally, the BER should be 0, signifying no change in bit values despite PVT variations.
The concept of using device mismatches for started in the year 2000 with the IC identification (ICID) [5]. Using delay differences due to random mismatch was shown to also give the same function with the arbiter PUF [6][7]. One of the most common delay-based PUFs is the ring oscillator (RO) PUF,[8] where the frequencies of a pair of ring oscillators are compared and decide the bit value (e.g. 1 if fB > fA). The power-on sate of memory elements can also be used to generate the hardware key, as demonstrated with the latch PUF[9], and more recently even for the RRAM crossbar[10]. Leveraging on the memory cell's metastability [11]. Other types of PUFs have also been explored, such as the VIA PUF[12] and oxide rupture PUF[13], to name a few.
| PUF Name | ICID | Arbiter | Latch | RO | INV_PUF | VIA | Oxide | RRAM |
|---|---|---|---|---|---|---|---|---|
| Type | Analog | Delay | Memory | Delay | Monostable | others | others | NVM |
| Technology (nm) | 350 | 180 | 130 | 65 | 65 | 180 | 55 | 130 |
| Worst Native Instability at Nominal Condition (%) | 1.3 | 4.82 | 3.04 | 2.8 | 2.34 | N/A | N/A | 0.0006 |
| Nominal Voltage | 2.5 | 1.8 | 1 | 1.2 | 1 | 1.8 | 1 | 5.5 |
| Maximum Instability under PVT Variation (%) | 5 | 4.82 | 5.46875 | 3.9 | 5.72 | -- | -- | 0.0006 |
| Voltage Range (V) | 1.1-5 | 1.8+/-2% | 0.9-1.2 | 1.2 | 0.6-1 | 0.01904 | 0.0000238 | 0.0006 |
| Temperature Range (C) | -25-125 | 27-70 | N/A | -40,25,90 | 25-85 | 1.6-2 | 0.8-1.4 | 2.5-5.5 |
| Bit Error Rate (%) | N/A | 4.82 | 5.46875 | N/A | N/A | 6 | ||
| BER after stability enhancement | N/A | N/A | N/A | N/A | N/A | 0.01904 | 0.0000238 | 0.0006 |
| Energy per bit (pJ/bit) | 8333.333333 | 0.17125 | 0.93 | N/A | 0.015 | N/A | 5.2 | 3.028 |
| Area (sq.um) | 23436 | 1468944 | 9450 | 241000 | 6000 | 1.06E+05 | 2.86 | |
| Bits | 112 | 64 | 180 | 3840 | 3040 | 128 | 8.19E+03 | |
| Area per bit (F2 / bit) | 1708.163265 | 708402.7778 | 3106.508876 | 14854.53649 | 6000 | 1.05E+06 | 218.2 | 169.2 |
| Bias | N/A | N/A | N/A | N/A | 0.5015625 | N/A | 0.5 | |
| Inter-PUF FHD | 0.4910714286 | 0.38 | 0.50546875 | 0.495 | 0.5013671875 | N/A | 1 | |
| Intra-PUF FHD | 0.013392857 | 0.02 | 3.04 | 0.028 | 0.0033636719 | N/A | 0.031 | 0.044 |
| # of possible CRPs | 132 | 4.5036E+15 | 1 | 256 | 11 | 1 | 64 |
Trends in PUF
Looking at PUFs implemented on ASIC, we can see that the majority of the PUFs are still weak PUFs, that is, they have limited challenge-response pairs (CRPs), as opposed to strong PUFs. Some of the trends in terms of area, stability and energy are shown in the figures on the right, and can be found in the PUFdb[14] and HWsecdb[15], which are public databases of PUFs, TRNGs and other hardware security implementations in ASIC.
Figure 2 shows the energy per bit and area per bit of existing implemented PUFs. These two metrics are important for resource-limited systems like WSN. It can be seen in Figure 3a that those with lowest energy to date are monostable PUFs, specifically the Automatic Self Checking and Healing (ASCH)[16] PUF and sub-threshold inverter[17]. In terms of area, the smallest are the memory bitcells, specifically the eDRAM PUF[18] and the ReRAM PUF[19].
One important property of PUFs is the bit error rate (BER), which specifies the percentage of bits that flip after several readings. Figure 3a shows the BER of weak PUFs implemented to date. The PUFs with low native BER are the memory PUFs, specifically the eDRAM PUF[20], with BER in the order of 10−5 and the eMemory[21]. These, however, are greatly reduced after applying enhancement techniques such as masking, ECC and majority voting. After stability enhancement, the BER can go an order lower, and the PUF with lowest BER after enhancement is the sense amplifier based PUF[22].
Curriculum and Manpower Development
As part of the objective of the CIDR program to continuously improve the curriculum and manpower, the topic on physically unclonable functions was incorporated in the EE 226 (Digital Integrated Circuits) as a possible area of research. The introduction lecture can now be found in youtube[23].
References
- ↑ T. Zia and A. Zomaya, "Security Issues in Wireless Sensor Networks," 2006 International Conference on Systems and Networks Communications (ICSNC'06), 2006, pp. 40-40, doi: 10.1109/ICSNC.2006.66.
- ↑ R. Maes, V. Rozic, I. Verbauwhede, P. Koeberl, E. van der Sluis, V. can der Leest, "Experimental Evaluation of Physically Unclonable Functions in 65 nm CMOS", in European Solid State Circuit Conference (ESSCIRC), 2012, pp. 486489.
- ↑ B. Chatterjee, D. Das, S. Sen, "RF-PUF: IoT Security Enhancement through Authentication of Wireless Nodes using In-situ Machine Learning", IEEE International Symposium on Hardware Oriented Security and Trust (HOST), 2018, pp. 205-208.
- ↑ A. Alvarez and M. Alioto, “Security down to the Hardware Level,” in Enabling the Internet of Things - from Circuits to Networks, Springer, 2017.
- ↑ K. Lofstrom, W. R. Daasch, and D. Taylor, “IC Identification Circuit using Device Mismatch,” ISSCC Dig. Tech. Papers, 2000, pp. 372–373.
- ↑ J. W. Lee, B. Gassend, G. E. Suh, M. van Dijk, and S. Devadas, “A Technique to Build a Secret Key in Integrated Circuits for Identification and Authentication Applications,” IEEE Symp. VLSI Circuits, 2004, pp. 176–179.
- ↑ D. Lim, J. W. Lee, B. Gassend, G. E. Suh, M. Van Dijk, and S. Devadas, “Extracting Secret Keys from Integrated Circuits,” IEEE Trans. Very Large Scale Integr. Syst., vol. 13, no. 10, pp. 1200–1205, 2005.
- ↑ R. Maes, V. Rozic, I. Verbauwhede, P. Koeberl, E. van der Sluis, and V. can der Leest, “Experimental Evaluation of Physically Unclonable Functions in 65 nm CMOS,” in European Solid State Circuit Conference (ESSCIRC), 2012, pp. 486–489.
- ↑ Y. Su, J. Holleman, and B. Otis, “A 1.6pJ/bit 96% Stable Chip-ID Generating Circuit using Process Variations,” ISSCC Dig. Tech. Papers, 2007, pp. 406–408.
- ↑ Y. Pang, B. Gao, D. Wu, S. Yi, Q. Liu, W.-H. Chen, T.-W. Chang, W.-E. Lin, X. Sun, S. Yu, H. Qian, M. F. Chang, H. Wu, "A Reconfigurable RRAM PUF Utilizing Post-Process Randomness Source with <6×10-6 N-BER," 2019 IEEE International Solid- State Circuits Conference - (ISSCC), San Francisco, CA, USA, 2019, pp. 402-403.
- ↑ S. K. Mathew, S. K. Satpathy, M. A. Anders, H. Kaul, S. K. Hsu, A. Agarwal, G. K. Chen, R. J. Parker, R. K. Krishnamurthy, and V. De, “A 0.19pJ/b PVT-Variation-Tolerant Hybrid Physically Unclonable Function Circuit for 100% Stable Secure Key Generation in 22nm CMOS,” ISSCC Dig. Tech. Papers, pp. 278–280.
- ↑ B. D. Choi, T. W. Kim, and D. K. Kim, “Zero bit error rate ID generation circuit using via formation probability in 0.18 µm CMOS process,” IET Journals Mag., vol. 50, no. 12, pp. 876–877, 2014.
- ↑ M.-Y. Wu, T.-H. Yang, L.-C. Chen, C.-C. Lin, H.-C. Hu, F.-Y. Su, C.-M. Wang, J. P.-H. Huang, H.-M. Chen, C. C.-H. Lu, E. C.-S. Yang, R. S.-J. Shen, “A PUF Scheme Using Competing Oxide Rupture with Bit Error RateApproaching Zero,” in IEEE International Solid State Circuits Conference (ISSCC), 2018, pp. 130–132.
- ↑ M. Alioto, A. Alvarez, "Green IC Physically Unclonable Function database," [Online]. Available: http://www.green-ic.org/pufdb.
- ↑ M. Alioto, “HW security primitives database," [Online]. Available: http://www.green-ic.org/hwsecdb
- ↑ Yan He et al. “An Automatic Self-Checking and Healing Physically Unclonable Function (PUF) with < 3x10−8 Bit Error Rate”. In: IEEE International Solid-State Circuits Conference. Vol. 64. February. 2021, pp. 506–508.
- ↑ Dai Li and Kaiyuan Yang. “25.1 A 562F2 Physically Unclonable Function with a Zero-Overhead Stabilization Scheme”. In: 2019 IEEE International Solid- State Circuits Conference - (ISSCC). 2019, pp. 400–402.
- ↑ Sami Rosenblatt et al. “Field Tolerant Dynamic Intrinsic Chip ID Using 32 nm High-K/Metal Gate SOI Embedded DRAM”. In: IEEE Journal of Solid State Circuits (JSSC) 48.4 (2013), pp. 940–947.
- ↑ Y Yoshimoto et al. “A ReRAM-based Physically Unclonable Function with Bit Error Rate ¡ 0.5% after 10 years at 125◦C for 40nm Embedded Application”. In: Symposium on VLSI Technology. 2016, pp. 256–257.
- ↑ Sami Rosenblatt et al. “Field Tolerant Dynamic Intrinsic Chip ID Using 32 nm High-K/Metal Gate SOI Embedded DRAM”. In: IEEE Journal of Solid State Circuits (JSSC) 48.4 (2013), pp. 940–947.
- ↑ Meng-Yi Wu et al. “A PUF Scheme Using Competing Oxide Rupture with Bit Error Rate Approaching Zero”. In: IEEE International Solid State Circuits Conference (ISSCC). 2018, pp. 130–132.
- ↑ Mudit Bhargava and Ken Mai. “An efficient reliable PUF-based cryptographic key generator in 65nm CMOS”. In: Design, Automation & Test in Europe Conference & Exhibition (DATE). Vol. 1. IEEE Conference Publications, 2014, pp. 1–6.
- ↑ https://youtu.be/JfNnSYuIOkc